In 2018, the Cambodian Ministry of Defence and several Vietnamese news outlets fell victim to a sophisticated cyberattack targeting multiple high-profile websites across Southeast Asia.
The attack went undetected for months, during which time anyone who visited the compromised sites was redirected to a page controlled by the hackers. From there, the hackers were free to distribute malware to the unfortunate victims. The notorious OceanLotus threat group claimed responsibility.
Known as a watering hole attack, OceanLotus was by no means the first group to target places people visit rather than the individuals themselves. In this article, we explain what a watering hole attack is, how they work, and how you can protect your business against them.
What is a watering hole attack?
Watering hole attacks are a type of third-party or supply chain attack. The hacker aims to install malicious software on the victim’s computer or gain access to their network by compromising websites they visit frequently. The consequences can be severe, ranging from theft of sensitive customer information to making the victim’s computer part of a botnet.
The name “watering hole attack” derives from nature. Over the aeons, lions and other predators have adapted their hunting strategies to conserve energy. Instead of chasing prey across the scorching African savanna, they simply wait for the zebra or gazelle to visit a watering hole and pounce while it’s busy drinking.
Cybercriminals typically use watering hole attacks to target large, well-protected organisations. Either by compromising an employee’s computer or a partner business further up the supply chain.
Watering hole attacks are difficult to detect because they harness the implicit trust people place in well-known organisations and institutions. And, because many successful attacks target exploits in browsers or systems, they have a high success rate.
Worried about the threat posed by supply chain attacks. Check out our guide to protecting your business.
How do watering hole attacks work?
The average watering hole attack unfolds over three stages.
1. Reconnaissance
The hacker gathers intelligence about the target’s browsing habits. This can include a mix of publicly available information and illegally obtained private data. They can then use this information to create a shortlist of suitable sites to host the attack. Usually, these are sites with lower-than-average security.
2. Planning
Once the hacker identifies the most suitable hosting domains, it’s time to decide how to launch the attack. The two most common options are to:
- Probe the shortlisted hosting domains for any potential weaknesses the criminals can exploit to compromise the legitimate website.
- Create a spoofed version or clone of a shortlisted hosting site that contains malware.
Some cybercriminals may combine the two approaches to increase their odds of success. In this scenario, the hacker compromises a legitimate website and inserts a redirect code that sends victims to the fake site where the payload is delivered.
3. Design and execution
The hacker exploits any weaknesses to insert malicious code into the watering hole site or cloned website. Typically, this involves manipulating web technologies like HTML and JavaScript or using exploit kits that target specific IP addresses. When someone visits the compromised domain, their browser automatically downloads the malicious software.
In the case of drive-by attacks, the hacker capitalises on the implicit trust users have in well-known websites by hiding malware in download buttons or links. When the victim clicks on the link, they inadvertently download the malicious software – often without even realising it.
Remote access trojans (RATs) are a popular choice of malware among cybercriminals, as this grants access to the victim’s computer or systems.
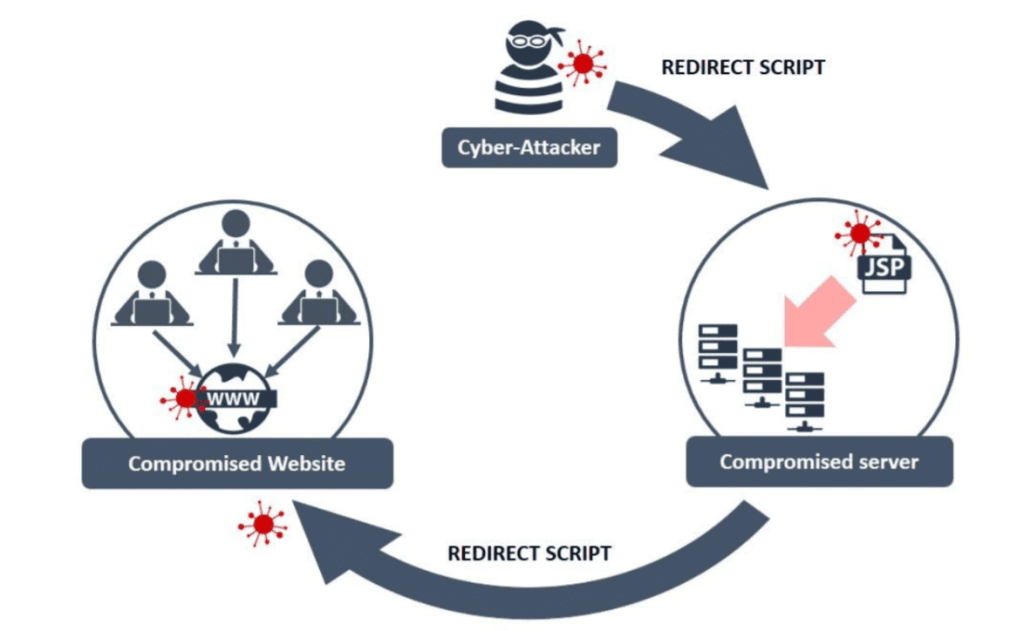
*Image: Supply chain security guidance, National Cybersecurity Centre
How to prevent watering hole attacks
The first step is to familiarise yourself with cybersecurity best practices. Simple measures, like installing reliable antivirus software and upgrading your browser protection, can significantly reduce your cyber risk.
We recommend adopting these four measures, as a minimum.
Stay on top of system updates
Many cyberattacks work by exploiting unpatched vulnerabilities in operating systems, browsers, and software. And watering hole attacks are no different. By installing the latest security updates as soon as they become available, you can plug these gaps before cybercriminals have a chance to use them.
Regularly review and test your security
Many cybercriminals bank on the fact that most people think their antivirus software tackles threats for them. We recommend that you review your security tools, processes, and policies at least once a year to ensure you’re protected against the latest threats.
Educate and train your staff
The cybersecurity landscape is dynamic. Cybercriminals are constantly evolving their tactics and new threats emerge all the time. Then, there’s the human factor. According to Stanford University research, human error causes 85% of data breaches. Run regular training workshops to teach staff to identify suspicious activity, spot potential threats, and respond to cyber-attacks.
Get Cyber Essentials certified
Cyber Essentials is a government-backed scheme that provides a simple framework to help businesses protect against cyber-attacks. It’s separated into five technical controls:
- Secure configuration
- Malware protection
- Network firewalls
- User access controls
- Security update management
Cyber Essentials is a more affordable option than advanced certifications, like ISO 27001. It’s also faster and less intensive, so it’s a good place to start. With the right guidance and support, you can become certified in just three days. This makes it the perfect solution for SMEs.
For more advanced recommendations, read the National Cybersecurity Centre’s (NCSC) 12 principles of supply chain security.
It’s a jungle out there
Watering hole attacks are no longer a niche threat. Forbes named them as one of the top ten cybersecurity threats of 2022, reflecting the increase in supply chain attacks in recent years.
The key thing to remember is that you’re not powerless. By adopting the measures we’ve recommended here, you can minimise your cyber risks and ensure you don’t fall prey to digital predators.