Malware is almost as old as the first personal computers. And like anything that’s existed for a long time, it’s easy to become complacent about it.
However, if your business has ever fallen victim to a malware attack, you’ll know how damaging it can be. The repair costs alone can set you back thousands; then, there’s the indirect financial impact of prolonged business disruption, data loss, and reputational damage.
Yet, it's not all doom and gloom. Armed with a little understanding, you can prepare your prepare your business and stay safe online. To help you do this, we've put together this short guide to help you get your head around the stages of a malware attack and how they work.
But first…
What is malware?
Malware is the umbrella term for malicious software that damages, disrupts, or gives cybercriminals access to a computer system.
Cybercriminals typically disguise malware as legitimate files, links, or attachments on a web page or email. The goal is to trick the victim into downloading the malicious program onto their device, where it can:
- Steal corporate information or sensitive customer data
- Delete or encrypt data
- Disrupt business operations
In some cases, malware can exploit vulnerabilities in your cybersecurity to spread to other connected systems in your network.
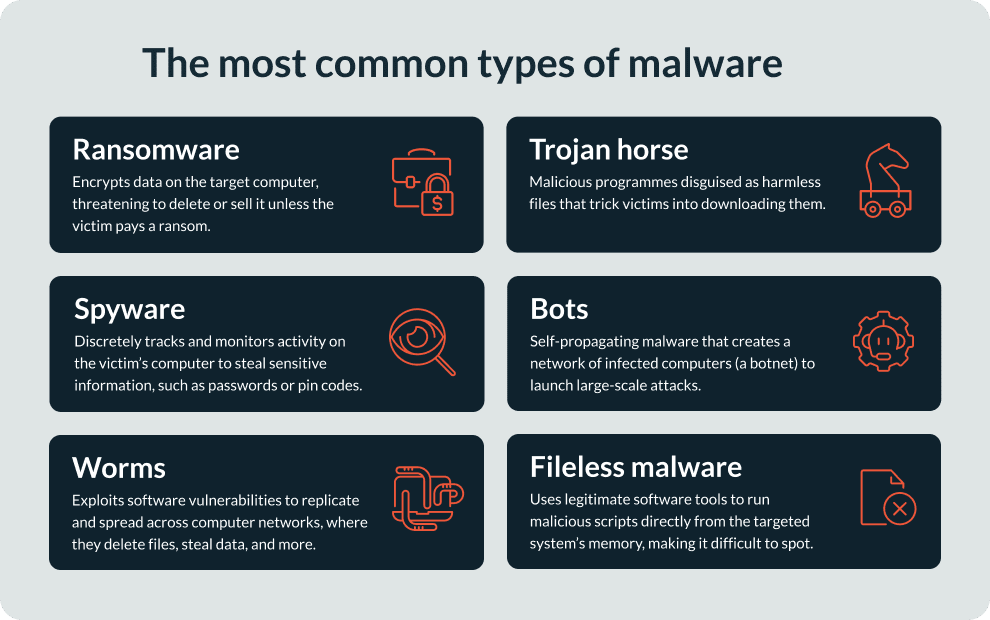
The most common strains of malware are:
- Ransomware
- Trojan horses
- Spyware
- Bots
- Worms
- Fileless malware
Considering Cyber Essentials but unsure where to start? Our guide is here to help.
There’s no getting away from malware
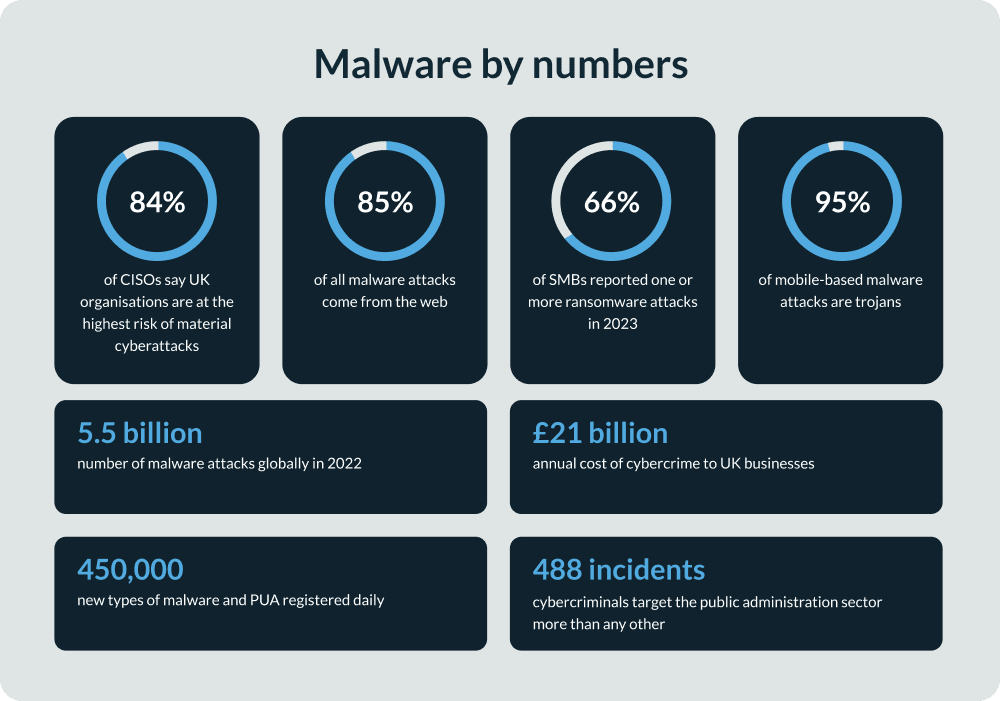
Malware is a pervasive threat. The AV-TEST Institute registers 450,000 new types of malware every day, contributing to the estimated 1.5 billion malicious software programs and potentially unwanted applications (PUA) in the world today.
Cybercriminals and threat groups are responsible for billions of malware attacks every year – there were 5.5 billion in 2022 alone. Cybercrime, including malware, costs UK businesses an estimated £21 billion every year.
UK businesses are on the frontlines of the malware threat. 84% of UK Chief Information Security Officers (CISOs) say UK organisations are at the highest risk of material cyberattacks, with ransomware among the most common. For example, 66% of businesses fell victim to one or more ransomware attacks in 2023, marking a 44% increase from 2020.
Meanwhile, public administration experiences more malware attacks than any other sector. Public sector bodies reported 488 separate incidents between November 2021 and October 2022.
The 5 stages of a malware attack
Infected websites, email attachments, and removable media are the most common means of malware attack. But whatever the approach, they all follow a similar five-stage pattern.
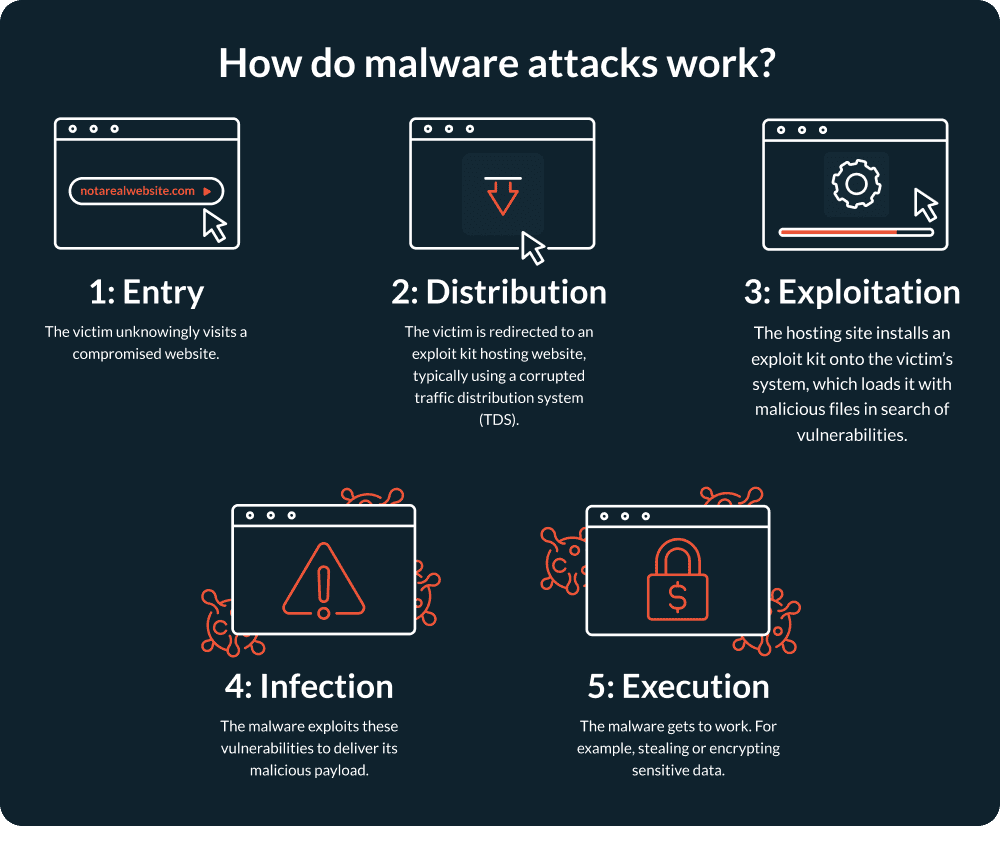
Stage 1: Entry
The victim inadvertently visits a compromised website by:
- Visiting a trusted website that a cybercriminal has hijacked
- Clicking on a link (often embedded in an email) that redirects the victim to the compromised website
Cybercriminals can compromise a trusted website by exploiting vulnerabilities in its servers or content management system (CMS) or using stolen credentials to inject malicious code. When the victim visits the compromised web page, the malware automatically downloads the code onto their systems.
Stage 2: Distribution
After bypassing the victim’s cyber defences, the malware redirects to an exploit kit hosting site. Cybercriminals typically use hacked traffic distribution systems (TDS) to create multiple redirections, which help to conceal their activities and the identity of their exploit kit hosting site.
Traffic distribution systems use a combination of traffic filtering and fast-flux networks to hide the host site from search engines and security scans, making them harder to track down and blocklist.
Stage 3: Exploitation
The hosting site installs an exploit kit onto the victim’s system, which loads it with malicious files, including:
- HTML
- Java
- Flash
These files probe the victim’s system, looking for vulnerabilities they can exploit to gain access to or control of the target computer. And the worst part? The technical barriers to entry for launching malware attacks get lower each year. Cybercriminals can create homemade exploit kits or, if they don’t have the coding skills, they can purchase them cheaply on the dark web.
Stage 4: Infection
Having successfully infiltrated the victim’s system, the malware delivers its harmful payload. This could be anything from ransomware to trojan horses or worms that operate silently in the background.
Stage 5: Execution
Now, the malware gets to its dirty work. Depending on the cybercriminal’s goals, this could be stealing or encrypting sensitive data to ransom back to the victim, disrupting business operations, or infiltrating other connected systems.
Malware attack examples
Malware affects everyone. Even global brands and government organisations with robust cybersecurity tools, practices, and policies have fallen prey to malware over the years.
These examples of recent high-profile attacks illustrate the extent of the threat.
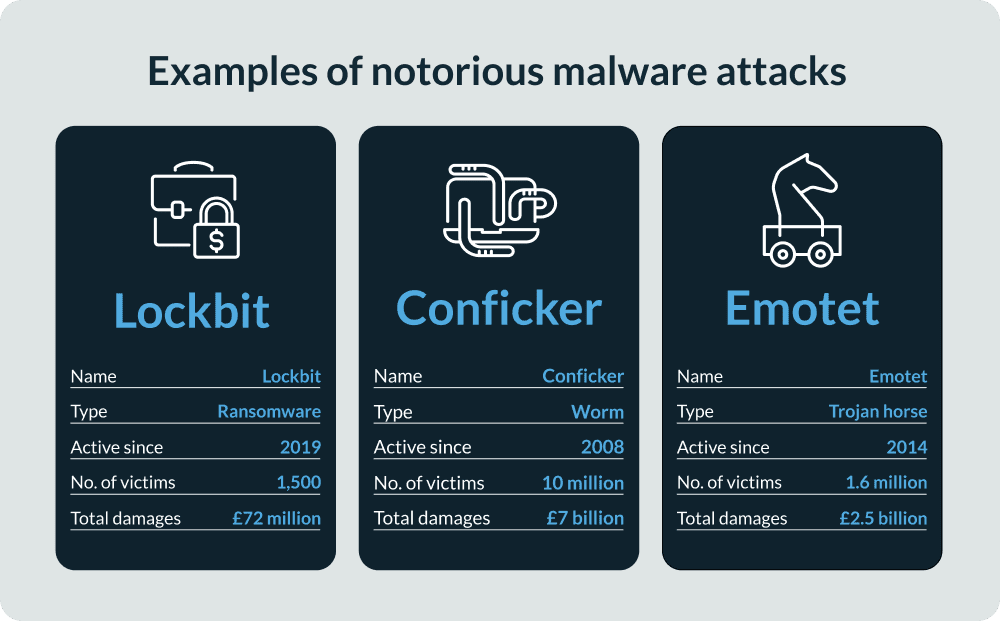
LockBit (ransomware)
One of the most active ransomware strains, LockBit has affected over 1,500 businesses at a total cost of over £72 million since emerging in 2019. The Royal Mail is among its most high-profile victims. At the start of 2023, LockBit caused severe disruption to Royal Mail’s overseas delivery service after it affected one of its back-office systems. The attack lasted two months and cost over £10 million to rectify.
Conficker (worm)
One of the largest and most notorious worms in history, Conficker has infected tens of millions of computers in over 190 countries since its discovery in 2008. Its long list of victims includes government agencies (including the UK parliament), businesses, and home computers, and remains an ongoing threat. To date, it’s caused £7 billion in damages.
Emotet (trojan horse)
First discovered in 2014, the Emotet trojan has wreaked havoc on businesses and government organisations, especially in the United States. According to the Department of Justice, the trojan has infiltrated over 1.6 million computers and caused £2.5 billion in damages.
Prevention is the first step to protection
It’s not always easy to spot a malware attack. Cybercriminals use sophisticated tools and techniques to conceal their activity from victims, so it could be days, weeks, or even months before you realise something’s wrong.
Preparation is the key to protecting your business, suppliers, and customers from malware. At the very least, we recommend regularly updating your systems and software, installing a network firewall, and teaching staff cybersecurity best practices.
If you want to go one step further, consider getting a cybersecurity certification. Schemes like the government-backed Cyber Essentials are quick, easy, affordable, and effective.
Want to know more about how cybersecurity certifications could help protect your business? Check out our guide to cybersecurity certifications in the UK.


