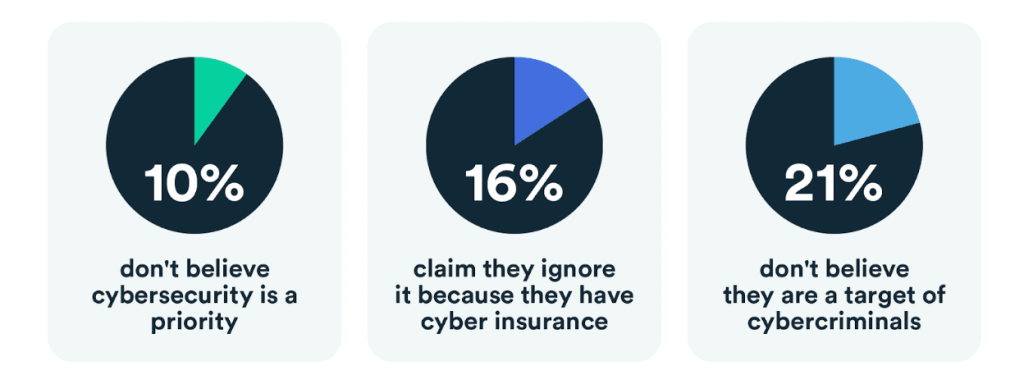
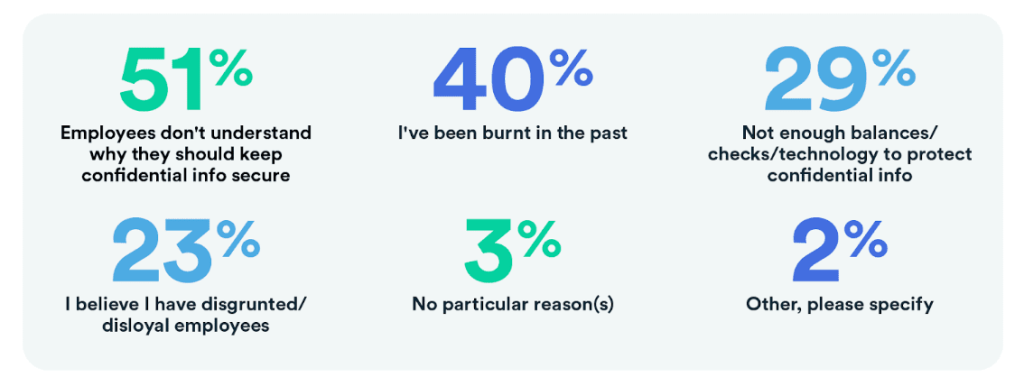
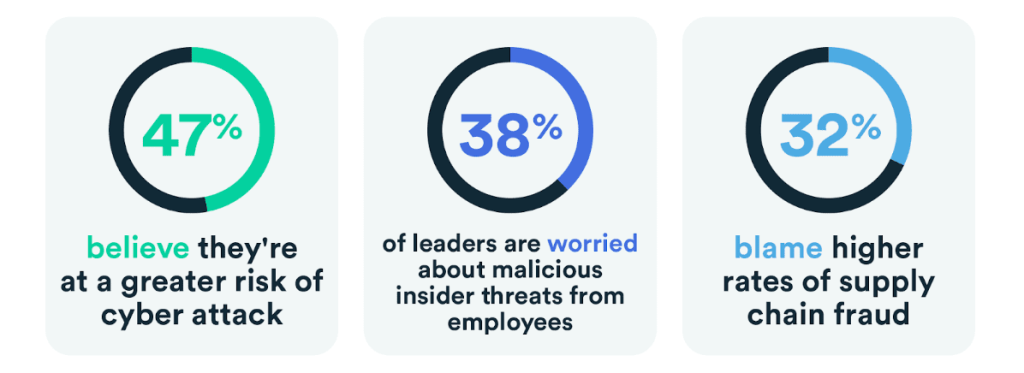
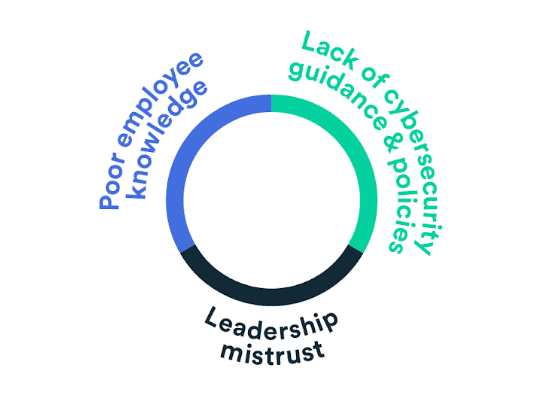
The most elusive of all malware; fileless malware is a threat you can’t afford to let slip off your radar. It accounts for 40% of global malware, according to research from Arctic Wolf Labs. And attacks increased by an eye-watering 1,400% between 2022 and 2023.
The next time you’re assessing cybersecurity priorities, keep protecting your business from these furtive attacks front of mind.
What is fileless malware?
Fileless malware is malicious code that’s written to your RAM or legitimate system tools rather than your disk (SSD or hard drive). Essentially, it uses your system’s software, applications, or protocols to launch an attack. Technically, it’s not actually fileless, but the name comes from where the code is stored and the fact it uses what already exists in the system.
The hacker will use the malicious code to gain access to your systems, execute the code by piggybacking on legitimate script, and steal credentials, encrypt files etc. – whatever they’ve set out to do as part of the attack.
Because code is stored in memory, it generally disappears when you reboot your system (unless the hacker uses more advanced tactics to make the malware stick around on restart). This makes the virus incredibly difficult to spot, meaning security teams and antivirus software may not notice or find out what caused the problem.
Want to know more about the threats facing small businesses like yours? Check out our latest report on SMEs and the cost of living crisis.
Some fileless malware techniques
Living off the land binaries (aka LoLBins)
LoLBins primarily refer to pre-installed Windows binary tools used for default system operations. PowerShell, a Windows scripting language, is an example of this. However, hackers can take advantage of them to launch attacks and avoid detection.
Memory code injection
A memory code injection inserts malicious code into a computer’s memory.
Fileless malware examples
Operation Cobalt Kitty
OceanLotus Group, who also go by APT32, targeted an international company based in Asia. The long-term attack compromised more than 40 computers and multiple servers.
They used the Windows PowerShell configuration management tool as an entry point for malicious code. It manipulated network management services so it would stay on systems rather than getting deleted on start-up. The group managed to penetrate the organisation via spear-phishing emails to senior employees that encouraged them to click on malicious links or download weaponized documents.
Fritz Frog
Fritz Frog is a fileless and serverless peer-to-peer botnet and worm that uses brute force to access secure shell (SSH) servers.
In January 2020, the cybercriminals behind it launched an attack that lasted for eight months, affecting 24,000 SSH servers from government, education, healthcare, and private enterprises.
Once the malware had successfully compromised a server, it would replicate and spawn threads to achieve different goals, e.g. one would use brute force to access more targets while another deployed the payload. It did this so it could run a cryptocurrency miner to process and steal cryptocurrency transactions from Monero.
Code Red
Identified as the first-ever fileless attack, Code Red spread worldwide in 2001 and affected more than 300,000 servers.
The worm exploited a Windows vulnerability and affected users of Windows NT, Windows 2000, and Microsoft IIS web server software. It caused websites using the webserver to display incorrectly.
According to a Sophos threat researcher, Microsoft released a patch to protect against the vulnerability just a month before the attack, showcasing the importance of updating software as soon as patches are available.
How to protect your business
Fileless malware is particularly tricky to detect because it’s written into memory or trusted, legitimate code. That means standard antivirus software doesn’t always detect a problem. And, in cases where the code is written to memory and wiped on restart, there’s no trace of the malicious code to work from.
However, there are some steps you can take to look after your cyber hygiene and give your business the best defence against malware in general, including fileless malware.
Patch your systems
Just like Code Red, unpatched vulnerabilities in operating systems, browsers, and software are a breeding ground for cyber threats. To counter this, install patches and security updates as soon as they’re available to give your business the best protection.
Continuous logging and monitoring
It’s important to stay on top of any security incidents so you have a full understanding of your IT infrastructure. It’s also important to monitor your systems for any unusual activity so you can respond to potential threats quickly and limit the damage. This can be difficult to do in-house unless you’re a very big business with lots of cybersecurity experience, but there are many options for third parties to monitor your security for 24/7 protection.
Education
To avoid threats, your people need to understand them. And the same is true for fileless malware. So, make cybersecurity training regular, bitesize, and as fun as possible. It’s not about fearmongering, it’s about arming your teams with knowledge.
Endpoint protection
An endpoint is a device that connects to and exchanges information with a computer network. Endpoint protection includes measures such as device encryption, perimeter security on cloud storage, network access control, anti-malware, and more.
Get Cyber Essentials certified
Cyber Essentials is a government-backed scheme with a simple framework based on five technical controls. Many of these controls include actions that overlap with our other tips in this section, so you can tick more off your to-do list in one go.
- Secure configuration
- Malware protection
- Network firewalls
- User access controls
- Security update management
It’s a great starting point for businesses looking to improve their cybersecurity credentials before moving on to more complex and costly certifications like ISO 27001. And, if you’re unsure which option is best for you, start by reading our free guide to certifications in the UK.
The fight against fileless malware
Hopefully, these tips help you to feel more confident about protecting your business against fileless malware.
However, as with all threats, fileless malware is ever-evolving. One way to ensure you stay cyber confident is to keep updated with information on new threats. Our report on SMEs and the cost of living crisis tells you everything you need to know about how small businesses are tackling cybersecurity during an economic downturn. Read it here.