Cybercriminals are always looking for the next sophisticated method to target businesses. And as a small business owner, it can sometimes feel impossible to keep up with the latest developments. However, knowledge is power, which is why we bring you regular updates. Let’s explore the latest trends in DIY cybercrime and Malware-as-a-Service, and how to mitigate them.
What is Malware-as-a-Service?
Malware-as-a-Service (MaaS) is a business model used by cybercriminals known as MaaS operators. MaaS operators lease their software, hardware, and related infrastructure to others for a fee. This enables malicious criminals to distribute pre-made malware, even with minimal coding skills.
You might’ve heard of similar terms like a Software-as-a-Service model, where an end-user purchases a pre-made software solution for their business or personal use. MaaS is the same concept but with malicious software. MaaS operators distribute the software on the dark web and sometimes even provide customer support to nefarious clientele.
Did you know that 47% of SME leaders feel more at risk of a cyberattack since the beginning of the cost of living crisis? Find out why in our latest report.
What is DIY cybercrime?
DIY cybercrime, or do-it-yourself cybercrime, is where a cybercriminal uses a pre-made solution to execute malicious activity. For example, they purchase ready-to-use Malware-as-a-Service, quickly get it up and running, and then use it to distribute malware to their target.
The worrying thing about DIY cybercrime is that anyone can purchase and use an off-the-shelf tool. It has never been easier for criminals to distribute malware, engage in phishing, and more.
At this point, you might be shaking your head and thinking, ‘D-I-WHY?!’ But don’t worry, all is not lost. You can dramatically reduce the threat to your business by putting the correct cybersecurity solutions in place.
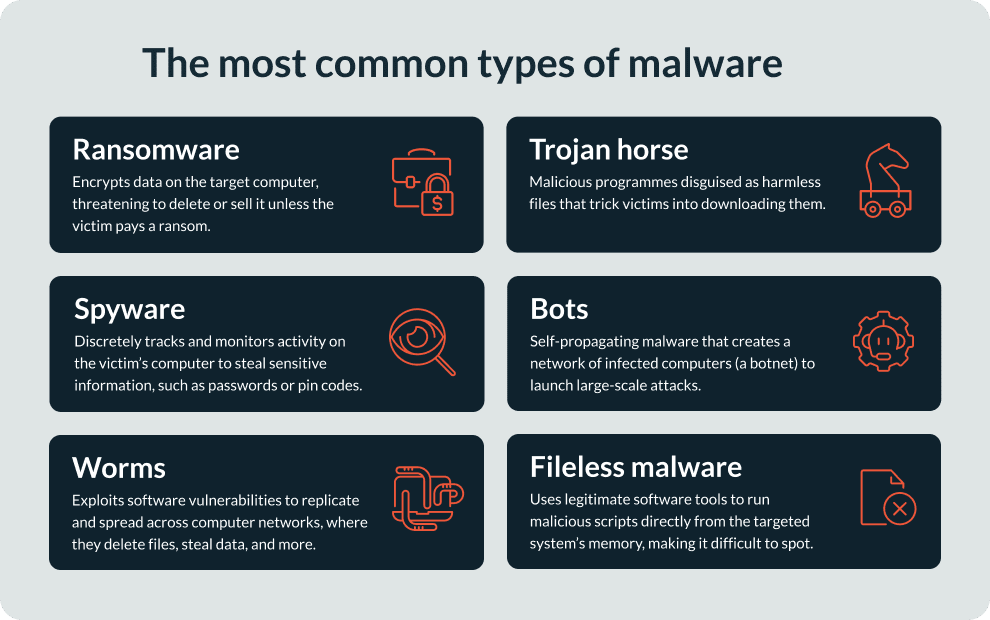
Malware-as-a-Service examples
ZeuS/ZBOT
ZeuS, or ZBOT, is a MaaS package that runs on Microsoft Windows. It was designed to steal sensitive information like banking credentials. First detected in 2007, it has successfully targeted large organizations like Amazon, Bank of America, and NASA.
SpyEye
SpyEye is a computer program that infects victims' devices and steals sensitive data. In a rare case of justice, the creator of SpyEye was caught and sentenced to nine and half years in US federal prison. However, this hasn’t stopped the presence of SpyEye across the internet.
Blackhole Exploit Kit
Released on an underground Russian hacking platform, Blackhole Exploit Kit made up 29% of all web threats in 2012, making it a significant threat. Since then, the exploit kit model has continued to transform and is still widely used by cybercriminals.
How to prevent Malware-as-a-Service attacks
Like all criminal activity, MaaS isn’t a threat that’ll soon disappear. But there are several simple steps to protect your business. Here’s what we think you should prioritise.
Educate employees
Most people don’t have in-depth knowledge of malware and DIY cybercrime. Due to the ever-changing nature of cybercrime, your employees must play a part in protecting your business. Make sure people know how to spot a malware attack in your business and provide them with training and resources so they stay informed.
Complete a cybersecurity certification
A cybersecurity certification, like Cyber Essentials, is an excellent way to quickly implement robust security measures in your business. This is because the steps to qualify help you attain certification status and proactively mitigate against malware.
Additionally, many companies find that the steps help them identify overlooked vulnerabilities in their business that they might otherwise be unaware of. It covers a broad range of factors like:
- Implementing data encryption
- Using firewalls
- Managing user access
- Updating software and operating systems
For more information on accreditations, we recommend reading our guide to cybersecurity certifications in the UK.
Monitor your security round-the-clock
Certification is a great starting point for putting in place the right defences and building your cyber confidence. However, cybercriminals won't only attack on certification day, so you need a way of monitoring your defences year-round. You could approach this manually, but beware it'll be time-consuming and require familiarity with cybersecurity best practices.
An alternative is to use a cybersecurity monitoring service, like CyberSmart Active Protect, which checks for vulnerabilities around the clock and ensures everyone in your business is working safely. Likewise, a vulnerability management tool can help you get ahead of the latest developments in cybercrime.
Want to know more about the threats facing small businesses like yours? Then have a read of our SME cost of living crisis report. It's packed full of insight into how small businesses are defending themselves during an economic downturn.