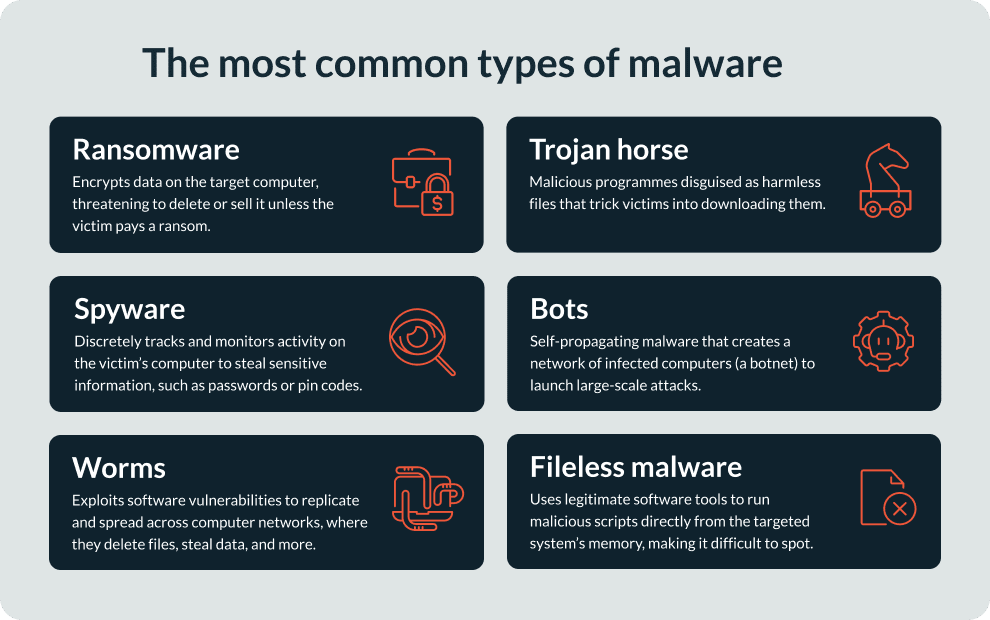
For many people, hearing the phrase ‘spear phishing’ conjures up images of intrepid divers hunting for their dinner in azure seas. However, much like ‘trojan horse’ the term has come to meet something quite different.
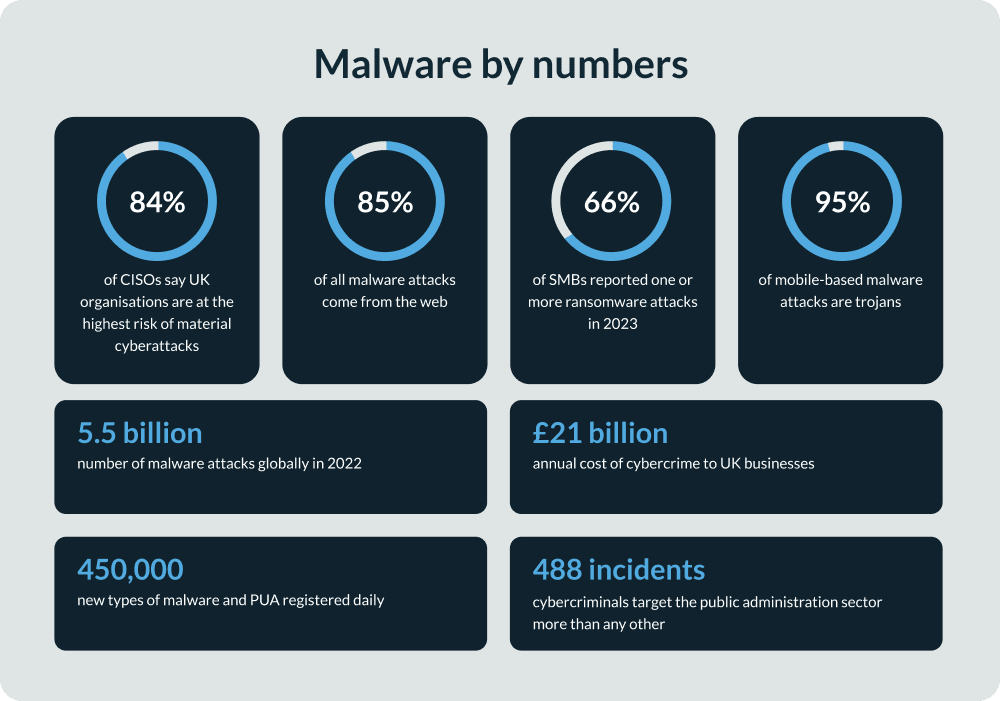
According to research, 50% of businesses were victims of spear phishing in 2022, with the typical organisation receiving 5 attacks daily. So the threat is real. But how does a spear phishing attack work? How does it differ from a phishing attack? Most critically, what can your business do to protect itself?
How a spear phishing attack works
Spear phishing is a form of phishing attack. However, unlike the ‘spray and pray’ approach of a conventional attack, spear phishing targets specific individuals, usually within a single organisation. The ‘spear’ in its name reflects this specific targeting.
A spear-phishing attack typically aims to gain privileged access. This is used to steal sensitive data or infect the target (and often their wider network) with malware.
Unlike your common-or-garden phishing attack, spear phishers assiduously research their targets. They do this so that the eventual attack appears to come from a trusted source, such as a boss or client. Spear phishing also uses social engineering techniques to dupe the victim into clicking on a link or granting access.
Let’s delve a little deeper into how it works.
Trying to protect your business on a budget? Start by reading our guide.
Anatomy of a spear phishing attack
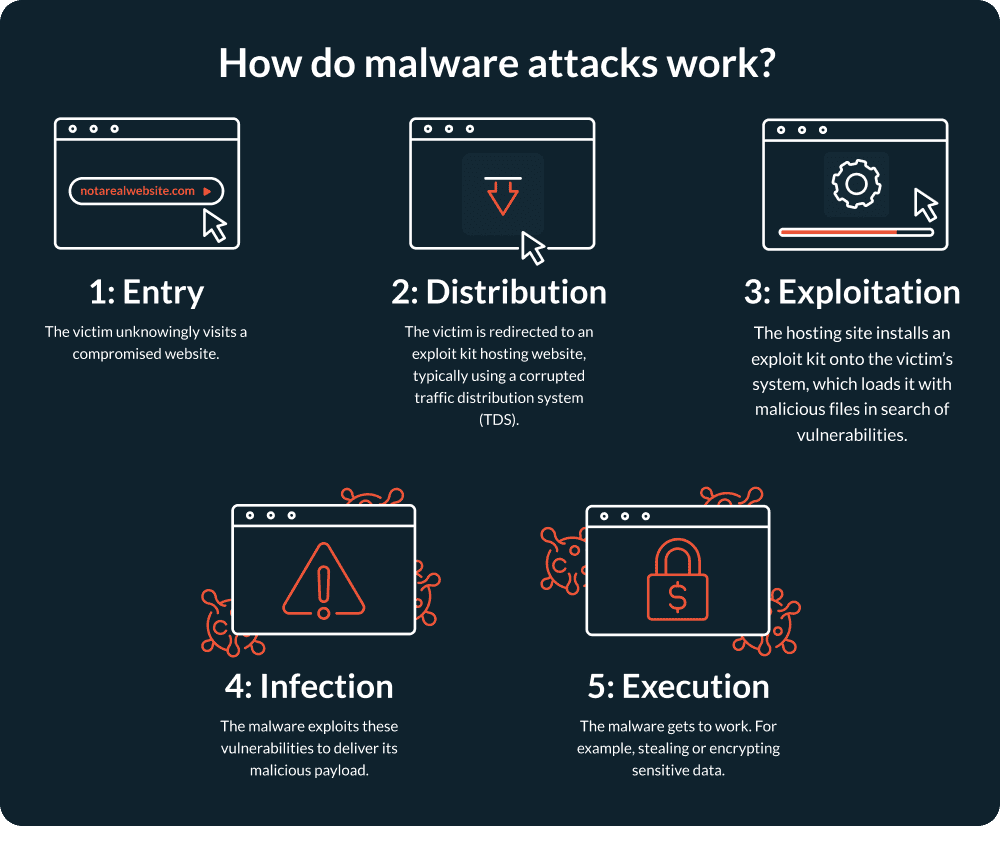
We’ve established what a spear phishing attack is, but how do they work? Typically, a spear phishing attack has five stages. These are:
1. Goal setting
The first stage is a simple one. After deciding to turn to crime, the bad guys start by plotting out what they want to achieve with the attack. It could be stealing ransomable data, causing disruption or myriad other goals.
2. Picking the target(s)
This stage usually involves a round of preliminary research. Which organisation should they target? Who works at the business they want to target? Are they likely to have access to the data or systems they want to access? Who are the senior leaders within the target organisation? How can they be reached?
These are the questions a cybercriminal will seek to answer as they lay the groundwork. Once they have, it’s time to go a level deeper.
3. Building a profile of the victim(s)
By now, the cybercriminals should have a solid idea of which organisation they want to attack and who within it makes the best targets. Next, it’s a case of getting to know their victims.
Spear phishers scour social media profiles and platforms like LinkedIn to discover contact details, the victim’s network of family and friends, business contacts, where they shop or bank, and even places they frequent. This information allows cybercriminals to build a rich profile of who the target is, allowing them to tailor the scam specifically to the victim.
4. Initiate contact and use social engineering techniques
Now the scheme has been devised, the cybercriminals launch their attack. Spear phishing emails usually use social engineering techniques such as creating a sense of urgency, trust or authority. The key to a good spear phishing scam is that it appears legitimate because the ‘sender’ is an individual or company the victim regularly engages with and contains at least some, authentic information.
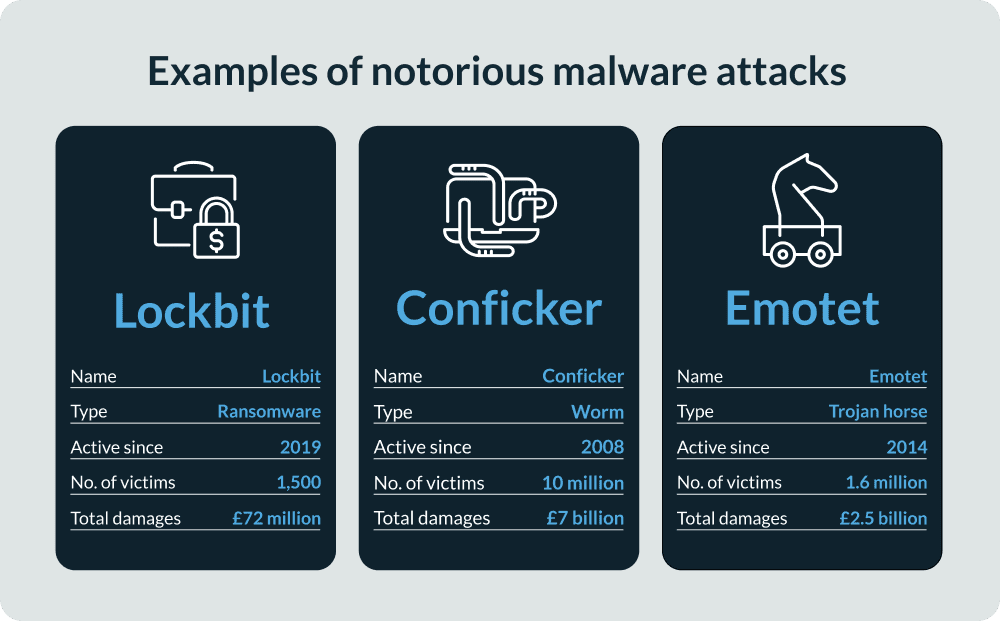
The most expensive spear phishing attacks of all time
1. Google and Facebook
This is perhaps the most famous phishing scam of all time. Between 2013 and 2015, Google and Facebook fell prey to a £77m Spear phishing campaign. Essentially, a Lithuanian cybercriminal named Evaldas Rimasauskas posed as an Asian supplier of both companies, sending fake invoices to key leadership figures within the tech firms.
Rimasauskas was eventually caught but not before he’d managed to defraud two of the largest companies in the world out of an eye-watering sum.
2. Ubiquiti Networks
In 2015, networking giant Ubiquiti was hit with a £36.7m spear phishing campaign. According to the company’s statement on the breach, it resulted from “employee impersonation and fraudulent requests from an outside entity targeting the Company’s finance department.” In other words, the company fell victim to a classic spear phishing attack.
3. Colonial Pipeline
Of all the incidents on this list, the Colonial Pipeline attack in 2021 is the most sinister. It remains the largest publicly disclosed attack on US infrastructure to date. The breach was so serious that the US government considered it a national security threat.
The attack had several stages. First, the hacker group DarkSide discovered a vulnerability exposed in a previous breach. A Colonial Pipeline employee had likely used the same VPN password in another location, exposing the company’s network.
Next, the hackers used this password to access the Colonial Pipeline, stealing over 100 gigabytes of data in just two hours. Following this, DarkSide injected the network with ransomware that infected several systems, including billing and accounting.
We don’t have a definitive figure for how much the breach cost Colonial Pipeline. We know the company paid DarkSide £3.47m for the decryption key for the ransomed data. However, the real losses could have been astronomical. Colonial Pipeline supplies oil to the entire US East Coast and the attack shut down its operations for a week. This meant the non-delivery of approximately 20 billion gallons of oil, worth around £2.7 billion at the time.
Spear phishing affects small businesses too
Although all of the examples above feature globe-bestriding businesses, this doesn’t mean there’s no threat to small businesses. Unfortunately, nothing could be further from the truth.
According to research, on average the employee of a small business will experience 350% more phishing and social engineering attacks than a staff member at a larger enterprise.
Why? Well, while cybercriminals are undoubtedly motivated by the prestige and financial rewards that come with the scalp of a global enterprise, small businesses represent an easy target.
SMEs typically have weaker defences and less developed cybersecurity practices than their corporate counterparts, for one. However, that’s not the only reason. SMEs' employees can often be turned more easily to a cybercriminal’s malicious ends, whether through actively colluding with criminals or negligence.
Indeed, CyberSmart’s research revealed that 22% of SME leaders believe employees are more likely to make mistakes – such as clicking on a phishing link – since the cost of living crisis began. Meanwhile, 20% believe employees will steal sensitive or proprietary data from the company to sell for profit or a competitive advantage.
How to protect your business
There’s no denying that small businesses are vulnerable to spear phishing attacks. Nevertheless, becoming a victim of this kind of breach isn’t inevitable. There are plenty of things you can do to ensure your business is protected.
1. Use a VPN
A virtual private network (VPN) is essential for remote working. If your business employs anyone who accesses company systems through a network that isn’t your own, even if only occasionally, you need one. Unsecured networks pose a huge threat to your business which a VPN can easily counter.
Rather than using the public network, a VPN routes your traffic through specialised servers and encrypts your data. This makes it virtually impossible for cybercriminals to break in through a public network (unless they have the password or encryption key as we saw in the Colonial Pipeline case).
2. Staff training
As mentioned earlier, Spear Phishing relies on social engineering techniques, using our human nature against us. This is tricky to counter, but not impossible. Cybersecurity awareness training can help your people recognise when they’re being targeted and give them the skills they need to avoid it.
3. Patch all software
Patching is very important to cybersecurity and the good news is that it’s simple. All you need to do is update all software with the patches providers release. This will stop cybercriminals from exploiting any vulnerabilities in providers’ software to access your business.
4. Deploy MFA
Like VPNs multi-factor authentication (MFA) adds an extra layer of security for your business, making it much harder for hackers to gain access. You likely already use MFA in some aspect of your online life, it’s now a requirement for most banking accounts. But if you haven’t already, switch it on for any system or application your business uses.
5. Protect your network
Your network is the gateway to your business. It’s what spear phishers are ultimately trying to gain access to when they attack you. Through it, a hacker can access just about anything your organisation does. So protect it, and protect it well. The four most simple things you can do to strengthen your network immediately are:
- Install a network firewall to filter network traffic
- Use a VPN to encrypt network traffic
- Segment your network to eliminate single points of failure
- Regularly update your router’s firmware
6. Always use back-ups
If the worst does happen and a spear phishing attack succeeds in stealing information, data backups can mitigate the worst effects. Not only will it enable you to minimise disruption by getting systems back up and running quickly, but it’ll also weaken cybercriminals’ bargaining power if there’s a ransom to be paid.
7. Limit user access
Be careful to limit who has access to what within your business. Users should only have admin rights within a system or application if it's critical for their role. The reason for this is simple; if a cybercriminal compromises a user account through a spear phishing campaign, the fewer permissions that account has the less damage a hacker can do.
8. Tie it all together
If the list above appears extensive, don’t fear, there are methods which allow you to tie it all together. The first is to complete a cybersecurity accreditation like Cyber Essentials or ISO27001 certification. These certifications can help you put in place good cybersecurity practices (including all of the above) and build your cyber confidence.
However, you also need something that keeps your cybersecurity baseline consistently high, year-round. This is where everyday cyber protection tools like CyberSmart Active Protect can help.
Finally, none of this has to cost the earth. For more on how to protect your business on a budget, check out our guide.