The current economic climate has seen better days, but how are the UK’s small businesses weathering the storm? At CyberSmart, we’re curious about how the cost of living crisis has impacted cybersecurity and people in small businesses.
We tasked Censuswide with surveying 1,000 UK SMEs to find out how they’re coping. What followed is our ‘SME cost of living crisis report’. It explores:
- How confident businesses are about weathering the economic storm
- The financial limitations impacting businesses
- The impact on employees
- The key impacts on cybersecurity
- The state of cybersecurity investments
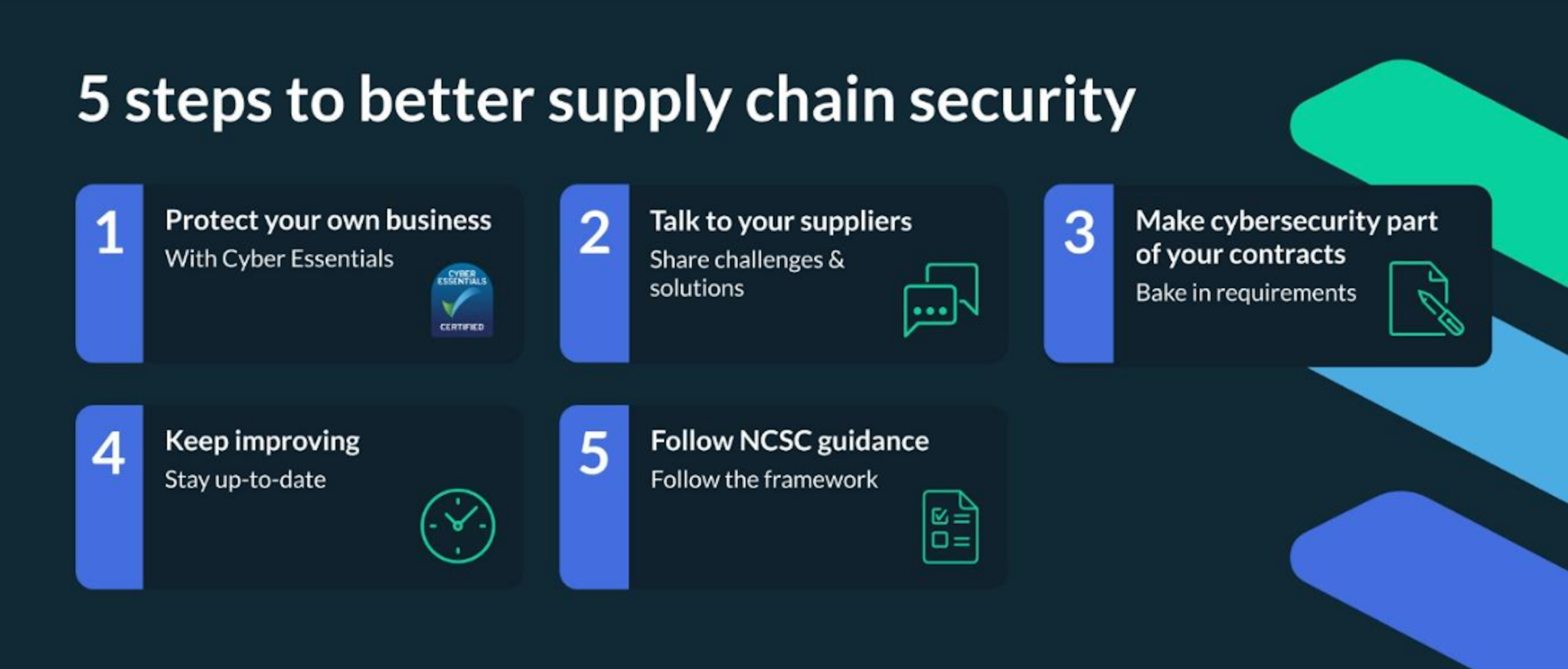
- How SMEs can approach cybersecurity in the cost of living crisis
Despite economic conditions, cybersecurity in your business doesn’t need to be all doom and gloom. Our report gives you the knowledge and understanding of the current climate to proactively protect your business. To help you, here are our key takeaways from the report.
Want to read the report in full? Get your copy here.
1. Cost-conscious businesses are looking for value
Small businesses must be cost-conscious. Careful budgeting and knowing when to invest is key to survival. And this means many small business leaders won’t invest in cybersecurity unless they know the payoff is worthwhile.
Understanding the benefits of strong cybersecurity is key in these conditions. Without a good level of understanding, decision-makers will overlook its importance.
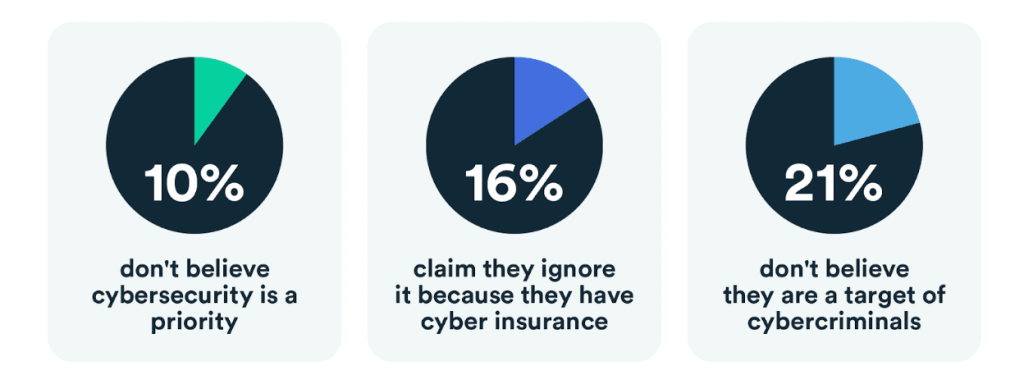
Understanding the benefits of strong cybersecurity is key in these conditions. Without a good level of understanding, decision-makers will overlook its importance.
2. Economic uncertainty raises threat levels
Even though businesses are overlooking the importance of cybersecurity, nearly half of UK SMEs (47%) believe they’re at greater risk of a cyberattack since the onset of the cost of living crisis.
Economic uncertainty has led to mistrust, too. 38% of leaders are worried about malicious insider threats from employees, while 32% blame higher rates of supply chain fraud. It seems that mistrust comes from inside and outside.
This is why increasing cybersecurity protocols and governance offers real business value. It provides much-needed reassurance that business data is safe, no matter where threats come from.
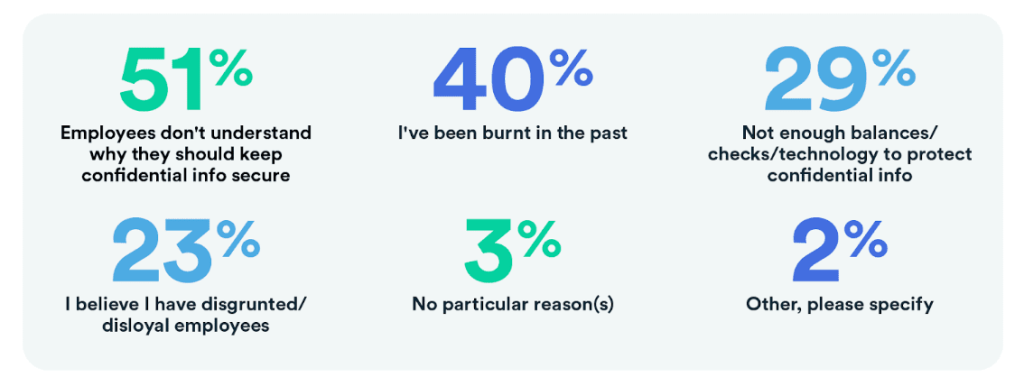
3. The employee skill gap is causing mistrust
Your employees are a line of defence when it comes to cybersecurity. But you must equip them with the tools and knowledge to counter potential attacks.
80% of respondents said that their employees do not fully understand why it is important to keep confidential information secure. And this lack of cybersecurity knowledge is the leading reason for mistrust.
The cybersecurity knowledge skills gap is a prominent factor for uncertainty. Of the 620 SME leaders who claimed to trust their employees, 25% still believe that staff pose the greatest security risk.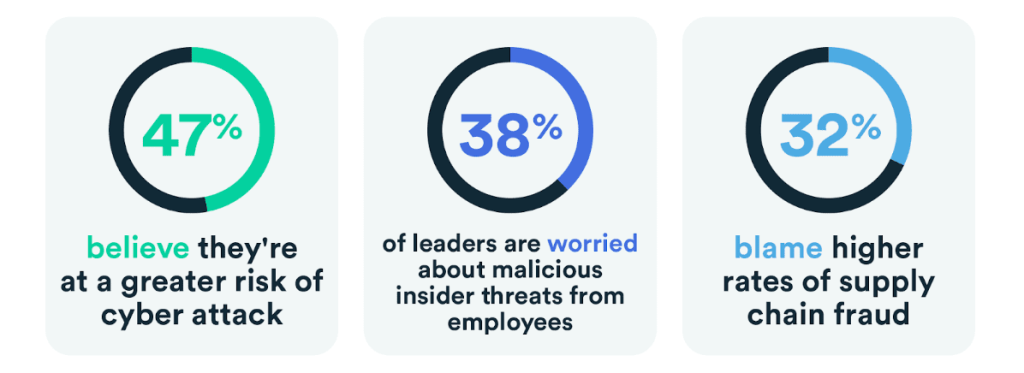
4. SMEs are missing important cybersecurity policies
We noticed that a lack of trust in employees, their cybersecurity knowledge, and no clear internal policies have an underlying impact on small businesses, so we did some digging.
Only 54% of SMEs have clear policies and procedures for sharing information and gaining access to confidential information. This means that just under half of SMEs don’t have important cybersecurity policies, at all.

It’s not surprising that leaders demonstrate a lack of trust in their employees, especially when there’s no guidance for the employees in the first place. Here, cybersecurity concerns appear as a vicious circle, and there’s an important gap in employee knowledge and a lack of policies. 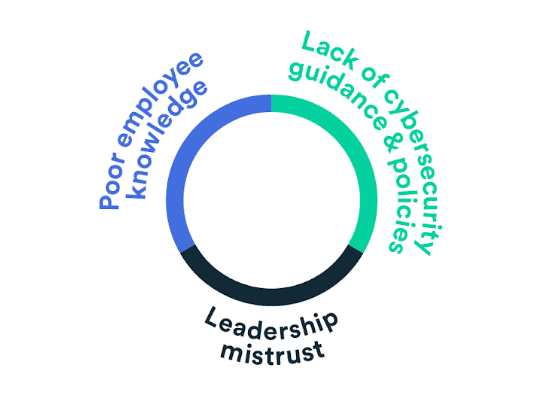
5. Basic measures can help to protect businesses
The report reveals that fixing basic, underlying issues can help alleviate the cybersecurity concerns as a result of the cost of living crisis. These issues are:
- Lack of employee cybersecurity training and resulting cyber confidence
- Missing cybersecurity policies, or too few policies
- Misunderstanding of the value of cybersecurity tools
Luckily, investing in cybersecurity doesn’t have to cost the earth. Instead, SMEs must be smart about their investments and increase cyber confidence for their employees.
Our report takes an in-depth look at these steps and how SMEs can implement them. These steps can help increase cyber confidence in your business and protect against cybersecurity threats.
Cyber confidence is key in the cost of living crisis
Uncertain economic conditions can make even the most stable business leaders feel on edge. Improving cybersecurity governance can help decision-makers protect their business and provide much-needed reassurance that their cybersecurity is under control.
Read our report today to learn more about the current concerns of SMEs in the cost of living crisis, and how to mitigate cybersecurity threats.